How to identify a phishing email
A phishing email is an attempt to get sensitive/restricted information by pretending to be a trusted source who is requesting the information for legitimate reasons. Attackers usually use email spoofing, creating an email with a forged sender address, to help create a level of trust with their intended target. They also tend to incorporate links to fake websites and/or malicious attachments into the messages they send.
Spear phishing is a more targeted than a standard phishing campaign. A standard phishing email is sent out to thousands -- if not millions -- of people claiming to be a person or company they have had dealings with in the past. An attacker who sends out spear phishing emails distributes them to a particular set of individuals and tailors the message as much as possible, based on their research of the victims targeted, to increase the probability of success. An attacker may use a standard phishing campaign to obtain access to an email account of a particular company so that they can send out spear phishing emails to their actual targets.
Phishing is a type of social engineering attack, which targets people (through psychological manipulation) rather than attacking computers to get what they want. Other social engineering attacks include, but are not limited to: pretexting, vishing, baiting, tailgating, and watering hole attacks.
A successful phishing attack could cause a variety of problems for Santa Fe College, depending on their tactic and which SF employee falls victim to the attack, including (but not limited to):
- Stealing SF login credentials (username and password)
- Infecting computers
- Stealing your, or all, protected employee data
- Stealing protected student data
Theft of an individual's SF credentials, depending on what they have access to, can be used to:
- Access any data that you have permissions to view
- Post false or inflammatory information on our website or social media, which would damage SF's image/brand
- Spread malware, including on our website or through our social media accounts
- Initiate a separate SPAM or phishing campaign using SF email accounts
- Divert money to/from SF to the attacker(s) own account(s), such as employee paychecks or grant money received
Infecting a computer on the SF network can be used to:
- Steal SF credentials or other restricted/protected information
- Attack our servers
- Attack servers belonging to other organizations using our Internet connection
- Encrypt or destroy data vital to our daily operations
- Render your computer to be completely unusable, which will delay you from doing your job and subsequently disrupt the college’s daily operations
Theft of an individual's data can be:
- Used to steal your identity, such as applying for credit cards in your name or stealing your tax refund
- Sold on illegal websites to others so they can steal your identity
- Used to divert money to/from your bank account to the attacker(s) own account(s)
- Used to gain access to your other accounts, such as your personal email or social media
- Attackers tend to use email accounts from legitimate email services, such as those provided by Google or Microsoft.
- Attackers change the wording in an email just enough so that it slips passed the filters used to catch such messages. Many attackers have their own copies of corporate email filters, which they use to test their emails before they send them.
- Attackers also use email spoofing to help evade filters by making the message look like it is coming from a trusted source. They can get a wealth of information about you from social media, questionable data brokers, and the contents of data breaches that have been posted online.
It is a good idea to treat all emails you receive with caution. Even if an email is coming from an address that you trust, their account could have been compromised by an attacker who is sending emails to people in that account's address book.
Here are some questions to ask yourself when you encounter these types of emails (clicking on the links will display an example image):
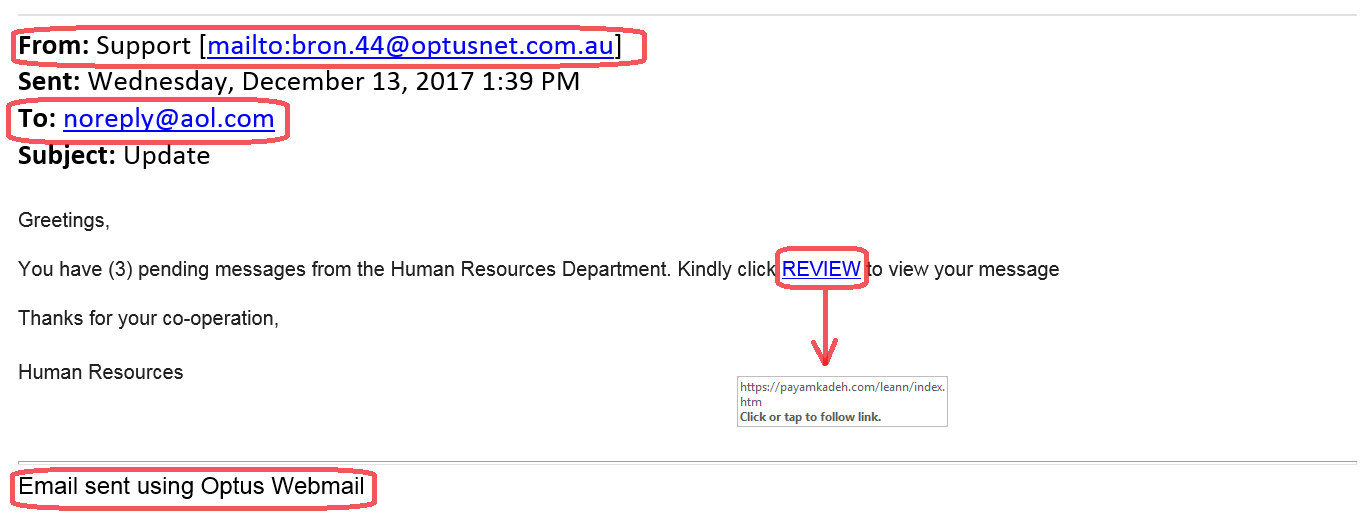
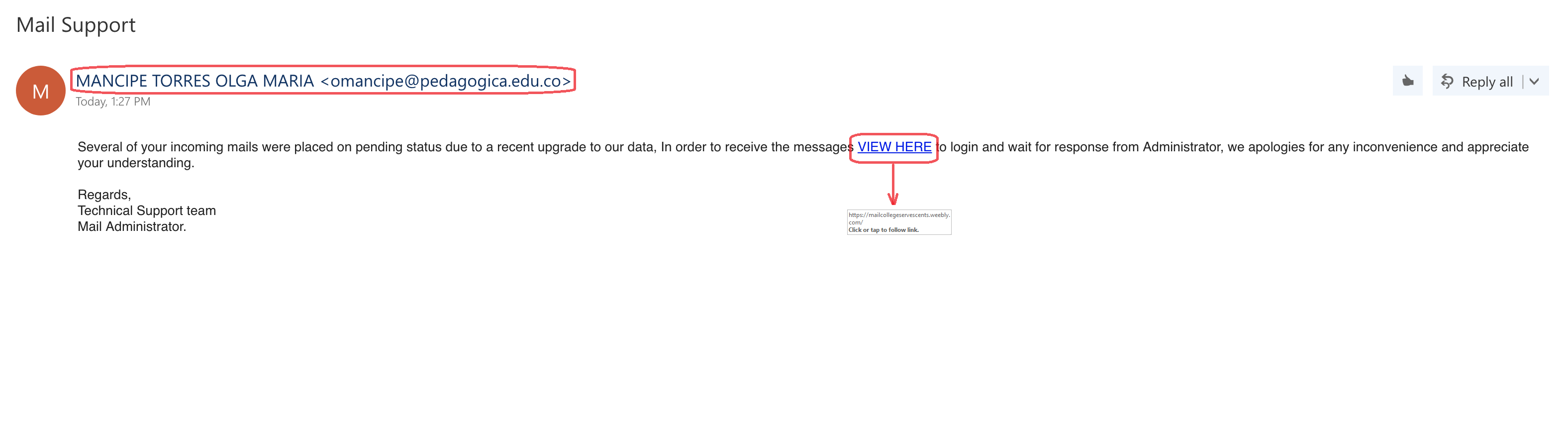
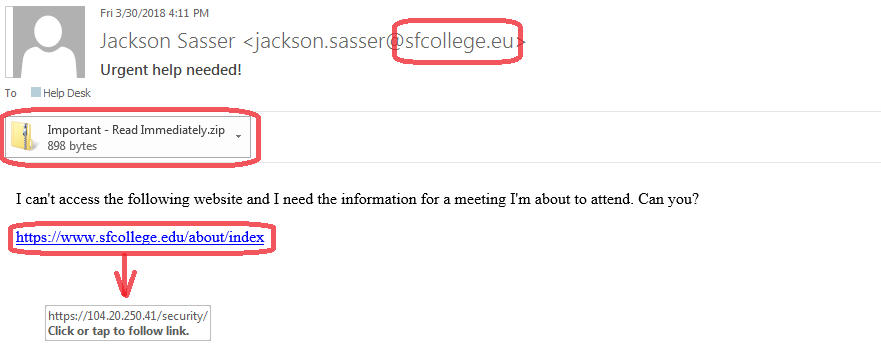
- Do you know the person who is sending the message?
- Do you recognize the sender's email address?
- Does the display name of the sender match the email address they are sending from?
- Is it identified as coming from a generic department name that would exist in almost all organizations?
- Is the email addressed to a non-SF email address or to a large number of (seemingly) non-related addresses?
- Is the email creating a sense of urgency to do something (reply to the message with personal information, click on a link, open an attachment, etc.)?
- If there is a link, do you recognize the web site it is trying to send you to? (put your mouse pointer over the link, but do not click it)
If there is ever any doubt as to whether an email you received is a phishing attempt, please do not hesitate to contact the ITS Help Desk. You can reach them by phone (352-395-5999) during normal business hours, or you can forward the email to them (help.desk@sfcollege.edu) anytime, day or night, and they will respond the next business day.
If you think an email is either SPAM or a phishing attempt, you can report it directly to Microsoft by using the Junk Email Reporting add-on in Microsoft Outlook by right-clicking on the email in question and selecting Junk --> “Report as Junk” or “Report as Phishing”. In webmail, you would right-click on the email and select “Mark as junk”.
You can also report SPAM to the Federal Trade Commission (FTC):
How to report spam to Microsoft manually
- Create a new, blank message and add the spam message as an attachment.
- Copy and paste the original spam message subject line into the new message subject
line.
Important: Leave the body of the new message empty.
- Send your new message to abuse@messaging.microsoft.com.
Important: Leave the body of the new message empty.
Here is the official Phishing site: cisa.gov/report
If you clicked on the link from a SF-owned computer or you provided your SF credentials to the attackers:
- Change your SF password immediately from another computer you know to be safe/clean
- Report the incident in detail to the ITS Help Desk (352-395-5999)
(Clicking on the image will display a larger version of that image)
Example #1
Example #2
Example #3